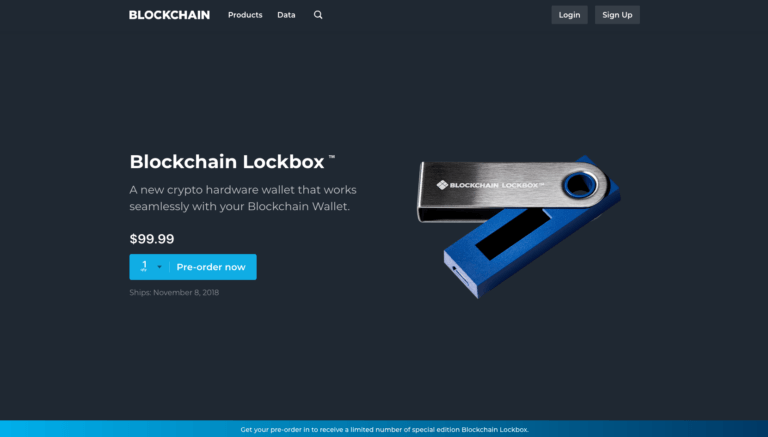
On Thursday (25 October 2018), crypto company Blockchain (formerly known as “Blockchain.info”), announced a new custom hardware wallet (“Blockchain Lockbox”) exclusively created for the Blockchain Wallet by French crypto hardware wallet specialist Ledger.
Here is how the news of this partnership was announced by Ledger on Twitter:
Big news: We’re excited to partner with @blockchain to create a new product, combining the power of Blockchain’s software and Ledger’s hardware: meet the #Lockbox. It’s a custom Ledger Nano S that's compatible with the #Blockchain Wallet.
Read more here: https://t.co/DhUEPlVxOy
— Ledger (@LedgerHQ) October 25, 2018
The press release was posted on Ledger’s blog, and provided the following details:
- “Blockchain Lockbox will allow Blockchain users to seamlessly and securely store crypto assets offline through a first-of-its kind integration of cryptocurrency hardware and software.”
- “The Lockbox offers Blockchain’s nearly 30 million users a tailored end-to-end solution that harnesses Blockchain’s innovative non-custodial software along with Ledger’s expertise in hardware security.”
- The Blockchain Lockbox, which is a customized Ledger Nano S hardware wallet, can be pre-ordered from today (with deliveries expected to take place around mid-November).
- Early orders will get a limited edition of the Lockbox (in blue).
- “Existing Ledger customers will be able to pair their Nano S devices to the Blockchain Wallet and benefit from the added functionality and ability to trade.”
Peter Smith, co-founder and CEO of Blockchain, said:
“The Lockbox is a reflection of what our companies both do best. We’ve created an elegant software and hardware integration that offers more functionality than previously existed in our space. We’re thrilled to offer the Lockbox to Blockchain users so they can easily manage their funds online and offline seamlessly.”
Pascal Gauthier, President of Ledger, added:
“With stories about crypto hacking continuing to dominate headlines, it’s obvious that security must be top of mind for all stakeholders in the crypto space. With the combined forces of Blockchain and Ledger, users are truly getting the best of both worlds. Our partnership with Blockchain is the first of its kind, but as two companies hyper-focused on crypto security, it’s one that’s a natural fit.”
Over on Blockchain blog, Peter Smith made a post titled “New Ways to Control Your Crypto”. Here, he first listed some of the things his company was company had achieved during the past six years:
- First “cross-platform, non-custodial, and cross-chain wallet”
- “30 million wallets in 140 countries”
- “Powering over $200 billion in consumer transaction volume and over 80 million consumer crypto transactions in the last two years alone”
- “Helping our users store millions of BTC, BCH & ETH coins and generate over a quarter of bitcoin network traffic alone”
Then, Smith said that at the end of last year, his company noticed that these were the most common requests from their users:
- “Better, faster ways for new users get their first crypto and make their first transaction”
- “More storage types, like hardware, as users’ balances increased”
- “More assets as users want to store and use an increasingly diverse asset set”
- “Better, more reliable sources of liquidity as trading and investing across assets continues to increase”
The Blockchain Lockbox, he say, is designed to address the second of these problems:
“Lockbox is simple to use and is even more secure thanks to a locked endpoint that prevents phishing and spoofing attacks. It’s hardware made easy, with a setup that takes just a few moments thanks to our custom hardware-software integration.
With Lockbox you’re able to check your balance and receive transactions, on mobile and web, without the inconvenience of having to plug your device in every time. In an industry first, you’ll also be able to trade directly from your Lockbox while still maintaining your keys. In conjunction with Lockbox, we’re also excited to let current Ledger device owners seamlessly pair with the Blockchain Wallet and trade directly from the Ledger device they already own.”
One unique feature of the Blockchain Lockbox hardware wallet is crypto-to-crypto trades. This is enabled via another new feature of Blockchain Wallet: “Swap by Blockchain”, which is “a next generation trading product with best-in-class liquidity and execution, powered by our new machine trading software platform that ensures best execution across assets.” This will allow Blockchain Wallet users to “have access to exchange-like prices without giving up control of their keys or their crypto”. Also, trade limits are being raised, “from hundreds to thousands of dollars of crypto per trade.”
Featured Image Courtesy of Blockchain